My brother Bob, founder of All Net Connect, preaches creating a “culture of security.” He has a point. Last week, All Net’s culture of security protected my bank account from a would-be “phishing” thief called “<halanjohnny3@gmail.com>”. (Do NOT send an email to that address.*) The story is instructive for anyone who gets email.
“Phishing” messages mimic trusted senders in order to steal sensitive information like passwords or account numbers. This particular thief sent emails to a number of All Net staffers, including Amy, who keeps the books. The email looked like this: “From: Bill Harlan <halanjohnny3@gmail.com>.” The fake “Bill Harlan” asked Amy to change my direct-deposit information and send my money to a different bank account, which was rude. Maybe even a felony.
The fraudulent request landed in Amy’s spam folder. That was good, but it didn’t land in everyone’s spam folder, which was bad. Amy, however, alertly checked between the angle brackets. She noticed that “<halanjohnny3>” didn’t match my regular email, so she notified Bric, an All Net senior administrator and a security expert. Bric and Amy quickly purged “halanjohnny3” from everywhere in the All Net system. (Halonjohnny3 had penetrated the system into a few places.)
All Net was made secure, and my direct deposits remained safe—thanks to spam filters, alert colleagues and especially thanks to a culture of security.
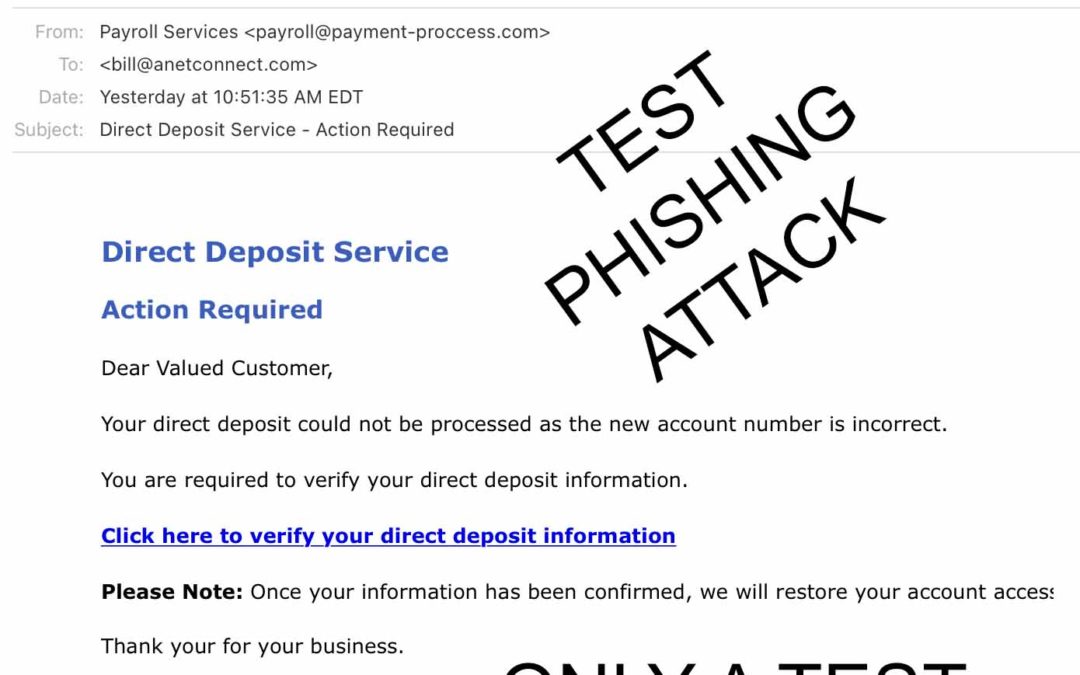
A few days later, Zach, an All Net administrator, generated a follow-up email. Using the KnowBe4 security training system, he crafted an official looking “Action Required” email from a phony company called “Payroll Services.” This email informed everyone at All Net that their “new account number” was incorrect. The fake spam message was only a test, which I passed—mainly by deleting it without replying to it or clicking the “handy” click-here button. I also told people about it. (Extra credit!). Anyone who did reply or click would have received an email from KnowBe4 about how to improve their security practices. That’s how KnowBe4 helps create a security culture.

And there’s more. A few days later, KnowBe4 invited All Net staffers to do a 10-minute online training session about defeating finance-related phishing attacks. I finished the session in nine minutes, learned a couple things and scored 100 percent on quiz. (I asked Bob if I had earned a cookie. He told me I first had to check the “accept all cookies” box.)
Bob and I were curious how “<halanjohnny3>” knew about my banking connection to All Net. After all, I’m not an employee. So I investigated. It turns out, I had mentioned on a social media site that I’m an occasional “communications consultant” for All Net. That information apparently had been scooped up by a company called “ZoomInfo,” which sells publicly available data about businesses to other companies to use for marketing. ZoomInfo has a webpage of information about All Net, some of which is accurate, some of which is not. For example, the page displays a logo and a spelling of the company name that All Net hasn’t used in years. More important, ZoomInfo also lists All Net personnel, complete with contact information—some of it correct, some of it wrong—including Bill Harlan, “communications consultant.” Mystery solved.
That’s the tiniest sliver of the kinds of public data readily available on the internet about all of us. That’s why Bob preaches about security cultures. Stay vigilant. Stay informed. Train regularly. ( KnowBe4 does affordable training.) However, if you get a message from <halanjohnny3>, you already know what to do.*
*What did I just tell you? Don’t email halonjohnny3 or anyone else that looks phishy. And always check <between the angle brackets>. By the way, I altered the spelling of “halonjohnny3” to protect the recklessly curious among you who thought, “What the heck, let’s see what happens. Hold my beer!”